For those of us in the cyber insurance industry, the close of 2009 and beginning of 2010 has been an exciting–and disquieting–time. The news has been saturated with reports of data breaches and cyber war scenarios. Clear public examples of cyber crime abound. In addition to news accounts, on a personal level most people are aware of, and may have even personally experienced, cyber crime. Most of us have received at least one data breach notification letter, informing us that our data has been exposed, and often offering credit monitoring or other services.
People everywhere are realizing that the Internet, so much a part of daily life at work and home that we take it for granted, is neither safe nor secure. We love the convenience of instant communication and information access, and we are not willing to stop using the Internet. But there is a significant dark side to this marvelous tool, and all businesses and individuals need to take steps to secure sensitive computerized information.
Any computer connected to the Internet is vulnerable to data thieves, just as every building is vulnerable to fire. Yet businesses that would not leave sensitive data in their reception areas fail to secure sensitive information that is computerized. Similarly, businesses that insure against fire losses fail to consider their cyber risks. As part of their renewals checklist, insurance agents and brokers may want to consider data security and other cyber risks, both for their clients and their own agencies.
How does it happen?
Most computer systems are vulnerable to attack by cyber thieves. Years ago, most attacks were annoying, but were more like pranks than serious crime. For example, an intruder flashes a message across the screen, and then the computer under attack fades to a blue screen. But from 2001's Code Red worm onward, malicious computer attacks have increased in frequency and severity.
Today's cyber criminals do not call attention to the fact that they have intruded. Cyber attacks happen in ever-changing ways. As security specialists develop and implement patches and other security measures to fight a particular attack, criminals develop new attacks. Most cyber attacks are stealthy, and involve launching malware, which is malicious software that is designed to intrude into a computer system without the owner's informed consent. Malware includes worms, Trojan horses, viruses, rootkits and spyware, among others. An example of a common attack is when malware installs itself on a server and monitors everything that goes through the server. The malware is designed to sniff for certain types of data, such as credit card or Social Security numbers. 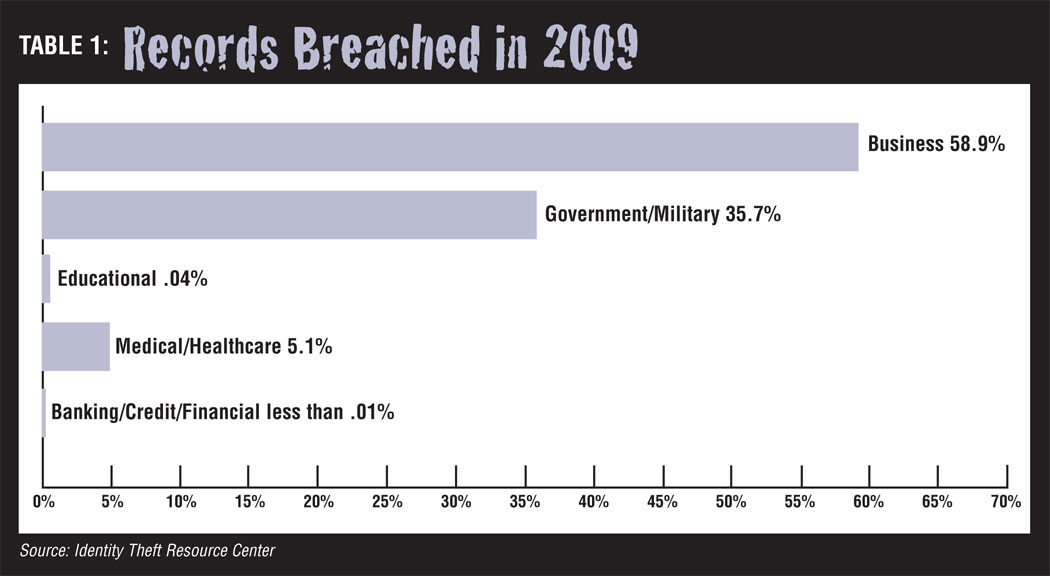
When the malware obtains the data it seeks, it forwards the data to the attacker. In most instances, the data is not forwarded directly to the attacker's computer. Instead, data is sent through a network of other computers that operate without the owners' knowledge or consent. A computer that is operated without the owner's consent is called a zombie. A network of zombies is called a botnet. According to recent reports, the Mariposa botnet, which appeared in December 2008 and was uncovered in May 2009 by Spanish authorities, involved 12.7 million PCs and spread to more than 190 countries. It reportedly is more sophisticated than the botnet that was used to hack into Google Inc. and other companies in the attack that led Google to threaten to pull out of China. Far from involving a few eccentric hackers, cyber crime today is big business.
The consequences of a data breach can be significant, even when the breach is small and doesn't lead to employee or customer identity theft. When a data breach is discovered, unless the sensitive information was encrypted, notification to the individuals whose data may have been exposed generally is required by law. In addition to federal laws and pending legislation, 45 states have laws that apply to data breaches. Along with informing customers that their sensitive data was breached, many states also require notice to their attorney general.
Media attention may further damage a business that is the victim of data theft. Press attention often follows notification, particularly if the breach is significant. Politicians also may issue press releases, explaining the steps they are taking to protect consumers from identity theft. Press reports following data breaches often inflict significant damage on a business. After reading about a significant data breach, many people are less willing to entrust their personal data to the breached entity. 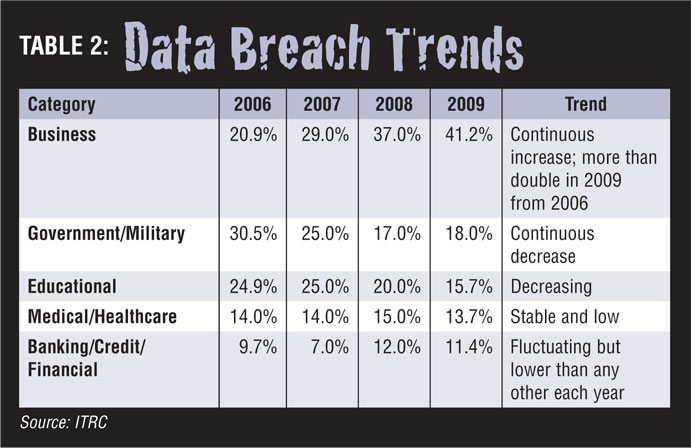
Notification of affected individuals and press attention may generate lawsuits, including class actions, which may be brought against a business that fails to secure the sensitive data. Plaintiffs assert that the business was negligent if it failed to comply with laws and regulations concerning data security, such as the federal “red flags rule,” which requires most businesses to have a written plan for securing sensitive data and responding appropriately if there is a data breach. When handled poorly, a data breach can destroy a business, particularly if it does not have insurance that clearly responds to first- and third-party losses stemming from a data breach.
Businesses generate most breaches
Many people think that cyber crime is largely limited to financial institutions and healthcare organizations. This perception is simply wrong.
Most data breaches do not happen to banking, credit, financial, medical or healthcare companies. Most data breaches happen to businesses. According to the Identity Theft Resource Center (ITRC), a nonprofit national organization dedicated to understanding and preventing identity theft, 498 data breaches exposing more than 222 million records were publicly reported in reliable sources in 2009. The banking/credit/financial category was responsible (See Table 1) for 57 breaches (11.4 percent of total) exposing 8,418 records (well less than 1 percent of the records exposed last year). The medical/healthcare category was responsible for 68 breaches (13.7 percent) exposing more than 11 million records (5.1 percent). Business was responsible for 205 breaches (41.2 percent) exposing 131,032,177 records (58.9 percent)–more than banks and hospitals combined.
Compared with other categories, the business category is doing a very poor job of securing data. Table 2, based on ITRC data for the number of breaches per year, shows the trend from 2006 through 2009. Clearly, business is a preferred target of cyber criminals.
A renewals cyber checklist
Businesses look to their insurance agents and brokers to help evaluate all of the exposures that the business faces. Insurance agents and brokers may wish to place cyber exposure needs on the punch list of items to discuss as renewals approach this year. Topics to consider include:
o What steps has the business taken to secure sensitive data?
o ??Has the business's board of directors approved and implemented a written red flags plan?
o Has the business evaluated contracts with outsource vendors for data security risk, to make sure data breach exposures are not inadvertently obtained when outsourcing services are purchased?
o How would the business's current insurance coverage respond to a data breach? If coverage is unclear, is this an area that needs to be clarified during renewal?
o Of the options available in the market, what cyber coverage is best suited to the business?
There are big differences in scope, kind and flexibility of breach response services between available cyber coverages, so many options are available for clients to consider.
Sometimes in the aftermath of a data breach, clients blame their agent or broker for failing to obtain coverage that expressly would have responded to a data breach or other cyber exposure. These situations often are avoided through routine communications that confirm in writing that you and the client discussed cyber exposures, and specify the actions taken as a result of the discussion. By asking clients to let you know if they want you to take any other or different action in connection with their cyber exposure, and keeping a paper copy of the communication, you will be prepared to refresh recollections if needed.
The best way to avoid data security problems is to take reasonable measures to protect sensitive information, whether that information is kept in paper or electronic form. Remember that the Internet is not a private form of communication. It's more like an old-fashioned party line telephone: you never know who is “listening in” and reviewing the content of your e-mails and other electronic documents.
It is shockingly easy for cyber criminals to obtain sensitive information from unprotected e-mail communication, particularly when the communication is wireless and made in a public location. Laptops and other portable devices also are easy targets for thieves. Businesses and individuals should take simple, commercially available steps to secure sensitive data. The steps to take depend on a number of factors, including the size of your operation and the kind and amount of sensitive data that you transmit. Password protections and key fob tokens frequently are used. Some operations prohibit storage of sensitive data on USB drives (also known as stick- or thumb-drives). Other operations have returned to communicating sensitive data by telephone rather than transmitting via unencrypted e-mail.
Prudent businesses should supplement their reasonable security measures by purchasing cyber coverage, just as prudent businesses purchase property insurance to supplement their building security measures.
Just as property insurance protects businesses from fire losses and often leads the way in improving building safety, cyber insurance protects businesses from data breach losses and encourages best practices by charging smaller premiums for businesses with better data security.
Want to continue reading?
Become a Free PropertyCasualty360 Digital Reader
Your access to unlimited PropertyCasualty360 content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Breaking insurance news and analysis, on-site and via our newsletters and custom alerts
- Weekly Insurance Speak podcast featuring exclusive interviews with industry leaders
- Educational webcasts, white papers, and ebooks from industry thought leaders
- Critical converage of the employee benefits and financial advisory markets on our other ALM sites, BenefitsPRO and ThinkAdvisor
Already have an account? Sign In Now
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.








